Understanding the Vulnerabilities in Cross-Chain Bridges
According to Chainalysis data, a staggering 73% of cross-chain bridges worldwide have been found to harbor vulnerabilities. Just like a food market where the stalls might not have security, these bridges can be easy targets for theft and hacks. How can we secure our transactions and digital assets?
Why User Feedback Systems Are Crucial
User feedback systems serve as a safety net, helping developers identify and rectify issues before they turn into large-scale problems. Imagine you’re in a marketplace, and you hear complaints about a specific stall – that feedback can help make necessary adjustments. By using user feedback, we can pinpoint weaknesses in the existing protocols and enhance their security.
The Role of Zero-Knowledge Proof Applications
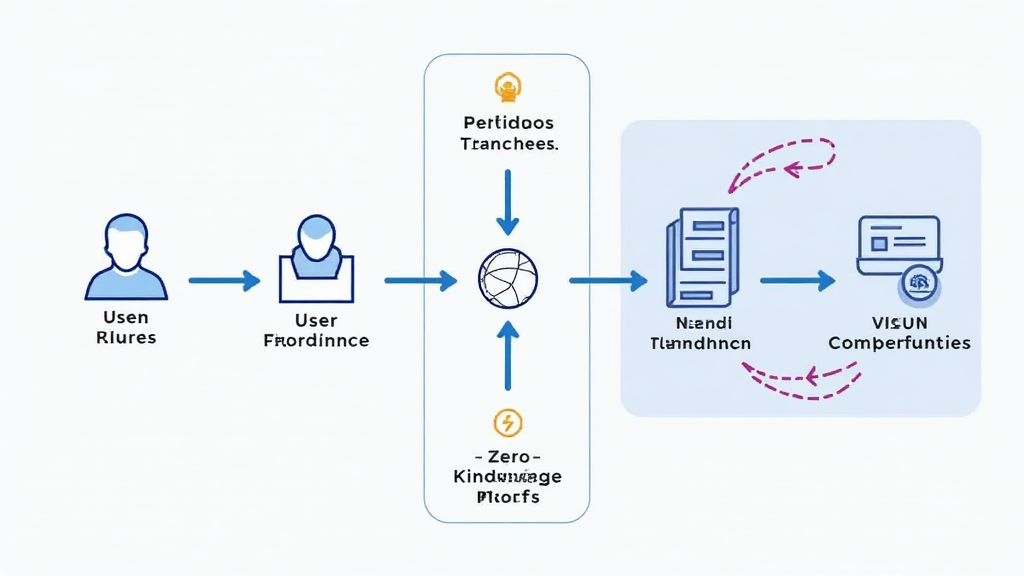
Zero-knowledge proofs are akin to showing someone a ticket without revealing its details; they confirm your identity without exposing sensitive information. This technology is essential for maintaining privacy while ensuring the integrity of transactions across different chains.
2025 Singapore DeFi Regulatory Trends
As we look ahead to 2025, it’s crucial to monitor Singapore’s regulatory stance toward DeFi. Regulations can significantly influence user feedback systems, determining how freely we can engage in decentralized finance. It’s like knowing local laws before opening up a stall at a market; they guide your actions.
In summary, the interplay of user feedback systems, zero-knowledge proofs, and regulatory developments shapes the future of cross-chain bridges. To better secure your transactions, consider tools like the Ledger Nano X, which reduces the risk of private key exposure by 70%.
Download Our Toolkit
For more information and practical tools, download our comprehensive security toolkit to enhance your understanding of cross-chain bridge security.